Do you ever wonder how easy it might be to obtain a password and get into your system? Once in the system, what can malicious parties do? Could they escalate their privileges to the administrator level? Hi, my name is Lisa Bock, and I’m a security ambassador. In this course, I’ll explore the third phase of ethical hacking, system hacking, an important phase for many reasons.
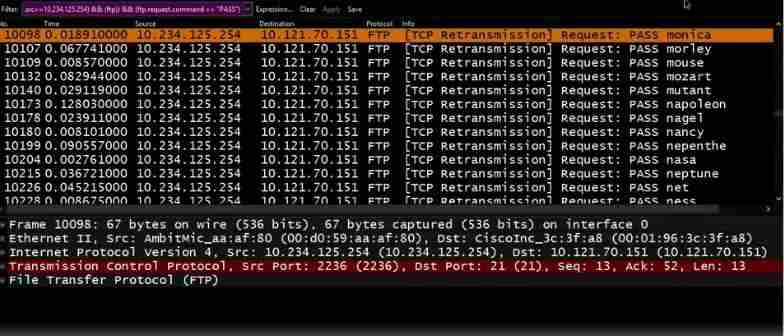
After scanning target systems, the ethical hacker is then armed with more information, and has a better idea of how malicious parties might get deeper into a system. In this course, I’ll go over methods to obtain a password, then once obtained, ways to escalate your privileges and execute applications.
I’ll cover spyware, capturing screen activity, and keystroke loggers. I’ll review ways of hiding in plain sight using alternate data streams and steganography. Finally, I’ll discuss ways to cover your tracks. This course is part of the