Bug Bounty Master Class
Companies are now spending million dollars on bug bounty programs.Read More →
Practical Windows Penetration Testing
Attacking & securing Windows systems with Metasploit and Kali LinuxRead More →
How to Create and Embed Malware
How The Hackers Create Malware to Hack Their Victim Machines (2-in-1 Hacking Course),Ethical Hacking,Penetration TestingRead More →
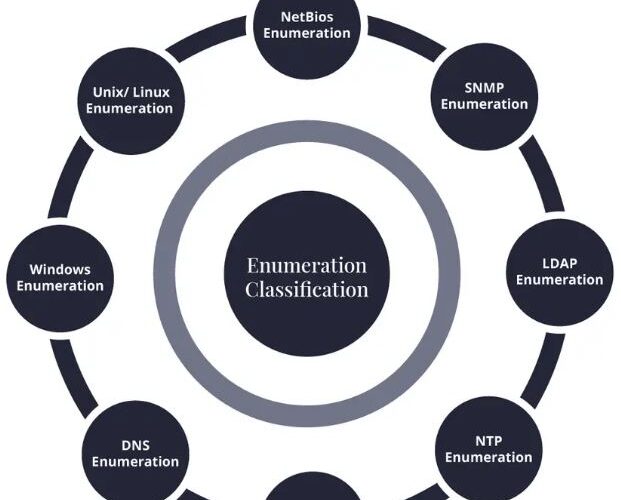
Ethical Hacking: Scanning and Enumeration
Enumeration is the most critical aspect of Ethical hacking. Read More →
Kali Linux Advanced Wireless Penetration Testing
wireless networks become ubiquitous in our livesRead More →
A Beginner’S Guide To Capture The Flag (Ctf)-2023
Start Learning in funny way ~ as a Cyber Security researcherRead More →
Threat Hunting with the Elastic Stack
It is recommended that you have a knowledge and basic understanding of the fundamentals of the Elastic Stack, as well as cyber security fundamentals.Read More →
Red Team: Weaponizing Windows Shortcut (Lnk) File Hands-On
Modern techniques to weaponizing windows shortcut (lnk) file for red team/penetration tester/ethical hackerRead More →